Fixxx
Moderator
- Joined
- Aug 21, 2024
- Messages
- 773
- Reaction score
- 3,683
- Points
- 93
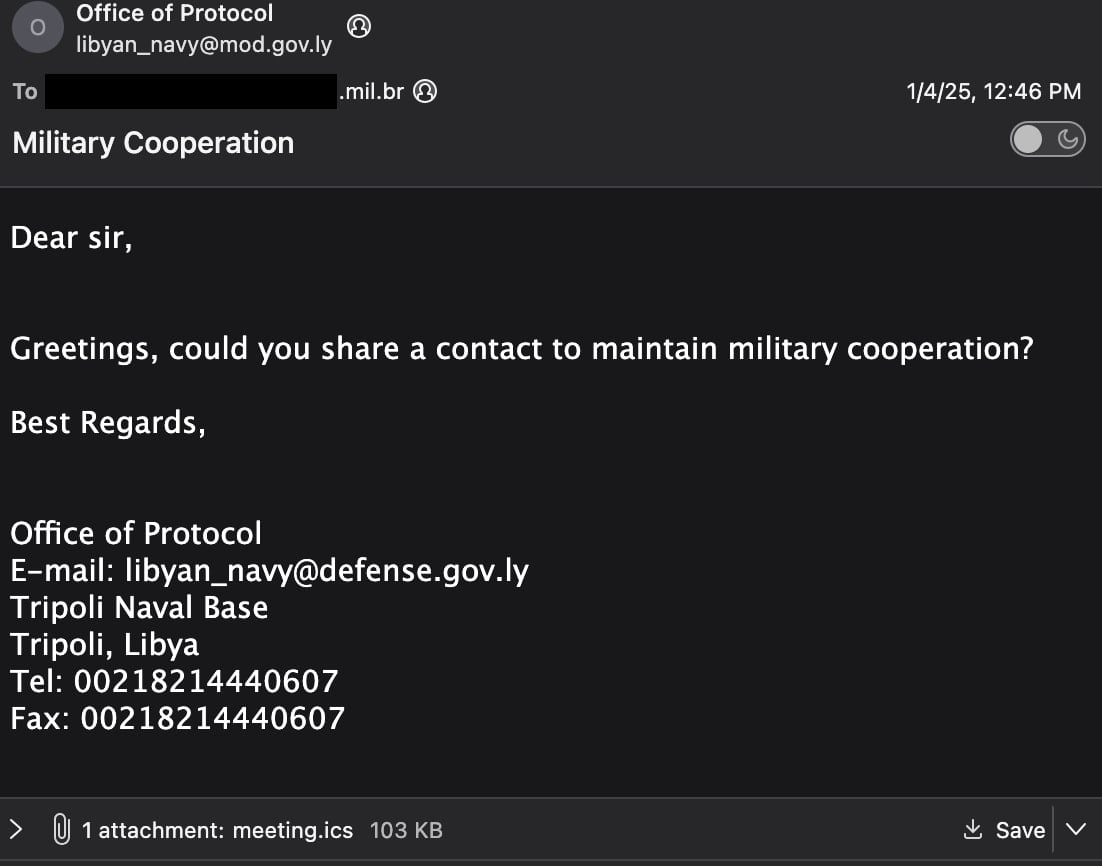
Researchers monitoring for larger .ICS calendar attachments found that a flaw in Zimbra Collaboration Suite (ZCS) was used in zero-day attacks at the beginning of the year. ICS files, also known as iCalendar files, are used to store calendar and scheduling information (meetings, events, and tasks) in plain text, and to exchange it between various calendar applications. Threat actors exploited CVE-2025-27915, a cross-site scripting (XSS) vulnerability in ZCS 9.0, 10.0, and 10.1, to deliver a JavaScript payload onto target systems. The vulnerability stems from insufficient sanitization of HTML content in ICS files, which allowed attackers to execute arbitrary JavaScript within the victim's session, like setting filters that redirect messages to them. Zimbra addressed the security issue on January 27 by releasing ZCS 9.0.0 P44, 10.0.13, and 10.1.5, but did not mention any active exploitation activity. However, researchers at StrikeReady, a company that develops an AI-driven security operations and threat management platform, discovered the attack after keeping an eye out for .ICS files that were larger than 10KB and included JavaScript code. They determined that the attacks had started at the beginning of January, before Zimbra released the patch. The threat actor spoofed the Libyan Navy’s Office of Protocol in an email that delivered a zero-day exploit that targeted a Brazilian military organization.
The malicious email contained a 00KB ICS file with a JavaScript file that was obfuscated using the Base64 encoding scheme.
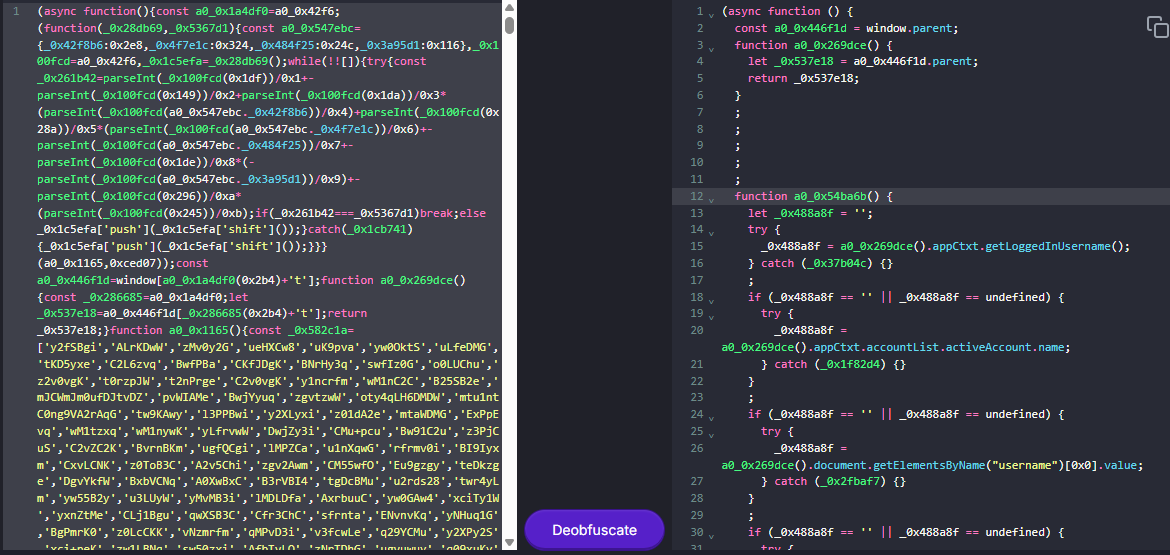
According to the researchers' analysis, the payload is designed to steal data from Zimbra Webmail, like credentials, emails, contacts, and shared folders. StrikeReady says that the malicious code is implemented to execute in asynchronous mode and into various Immediately Invoked Function Expressions (IIFEs). The researchers found that it can perform the following actions:
*malicious email sent by the attackers.
The malicious email contained a 00KB ICS file with a JavaScript file that was obfuscated using the Base64 encoding scheme.
*deobfuscating the JavaScript payload.
According to the researchers' analysis, the payload is designed to steal data from Zimbra Webmail, like credentials, emails, contacts, and shared folders. StrikeReady says that the malicious code is implemented to execute in asynchronous mode and into various Immediately Invoked Function Expressions (IIFEs). The researchers found that it can perform the following actions:
- Create hidden username/password fields
- Steal credentials from login forms
- Monitor user activity (mouse and keyboard) and log out inactive users to trigger theft
- Use Zimbra SOAP API to search folders and retrieve emails
- Send email content to attacker (repeats every 4 hours)
- Add a filter named "Correo" to forward mail to a Proton address
- Collect these authentication/backup artifacts and exfiltrate them
- Exfiltrate contacts, distribution lists, and shared folders
- Add a 60-second delay before execution
- Enforce a 3-day execution gate (only runs again if ≥3 days since last run)
- Hide user interface (UI) elements to reduce visual clues